pwnstack0x00
栈溢出0x00
buuctf前四题作为入门题
test_your_nc
测试nc的水题,略
rip
get函数栈溢出
1 | from pwn import * |
warmup_csaw_2016
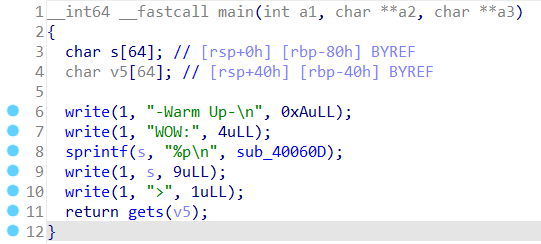
gets()函数说明有栈溢出漏洞
1 | int sub_40060D() |
调用这个函数可以获得flag,地址是0x40060D
1 | v5变量 |
所以要填充(0x40 + 8)个字符
exp
1 | from pwn import * |
ciscn_2019_n_1
还是一道基础的栈溢出题,没开栈溢出保护
1 | int func() |
这题应该是用v1溢出修改v2中的值,使得v2 == 11.28125
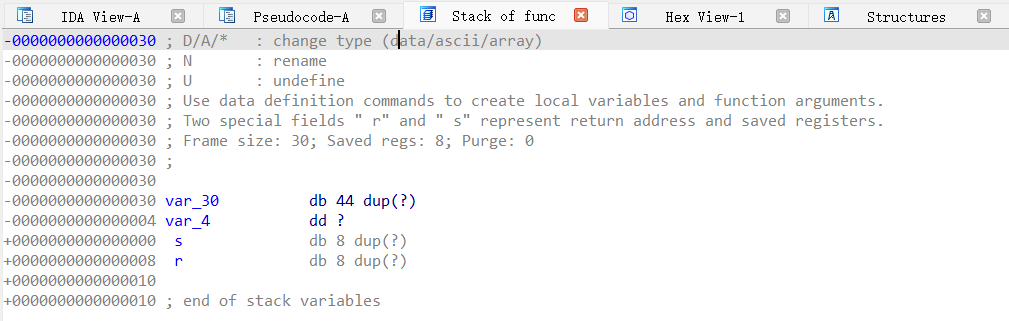
v1在函数栈中占据(0x30 - 0x04)的大小,v2占据0x04的大小
为什么伪代码注释中是[rbp - 30h]?
这是因为栈在内存中是从高地址朝低地址生长的,rbp是栈底指针

回归正题,把鼠标放到dword_4007F4就可以看到11.28125的16进制数值为0x41348000
exp
1 | from pwn import * |
You need to set
install_url to use ShareThis. Please set it in _config.yml.